Learn how to configure IPSEC site to site vpn on cisco router using cisco Packet Tracer.As we all know IPsec provides secure transmission of sensitive data over unprotected networks like internet.So what actually IPsec does is it acts at the network layer which means its working in network layer of TCP/IP model and protecting sensitive data and authenticate IP packets only between participating IPsec devices like cisco routers. here in this IPSEC Example lab Router0 and Router1 is is participating in IPsec peers.So in this activity or in this lab i will configure these two routers to support a site to site IPsec VPN for traffic flowing from their respective LANs.
While configuring this lab I consider that everyone who is going to configure this lab must know how to assign ip address on router interfaces and if you don’t you can read my articles on How to assign ip address on Router interfaces..
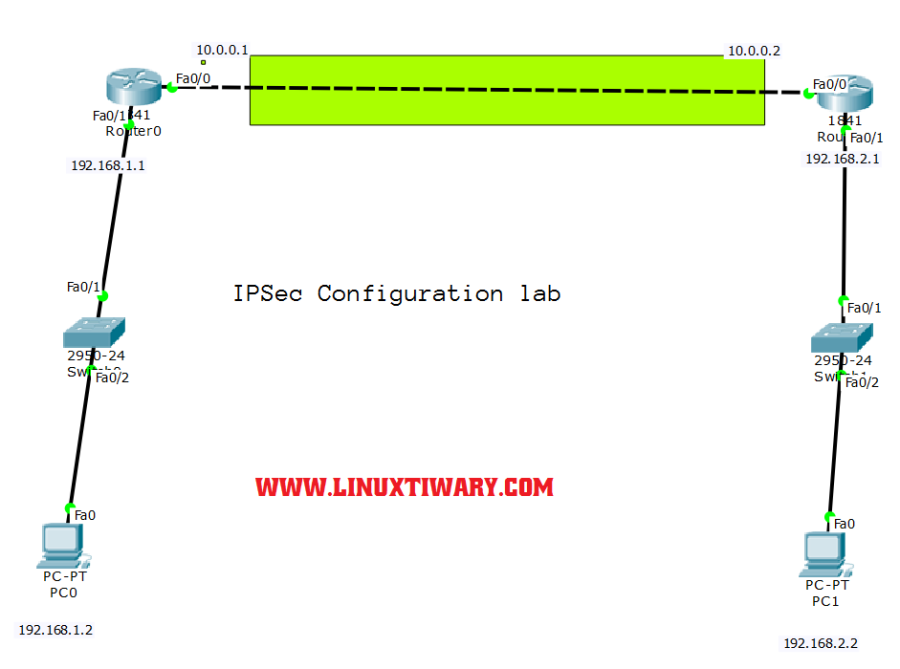
Step 1:configuration on Router0
Router(config)#router rip Router(config-router)#network 10.0.0.0 Router(config-router)#network 192.168.1.0 Router(config-router)# %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up Router(config-router)#exit
Step 2. ISAKMP policy
In this section we will Configure and decide what parameters will be used for the IKE phase 1 tunnel
Router(config)#crypto isakmp policy 10 Router(config-isakmp)#authentication pre-share Router(config-isakmp)#encryption aes 256 Router(config-isakmp)#group 2 Router(config-isakmp)#lifetime 86400 Router(config-isakmp)# Router(config-isakmp)#exit
Step 3. Transform Set
In this section we Configure and decide what parameters will eb used for the IKE phase 2 tunnel (aka the IPSEC tunnel)
Router(config)#crypto isakmp key redhat address 10.0.0.2 Router(config)#crypto ipsec transform-set TSET esp-aes esp-sha-hmac
Step 4:ACL (Access Control List
Here in this step we will Create an ACL to define what “interesting” traffic will be sent over the VPN
Router(config)#access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
Step 5. Cypto Map
Define and Configure using the previous parameters.
Router(config)#crypto map CMAP 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Router(config-crypto-map)#set peer 10.0.0.2 Router(config-crypto-map)#match address 101 Router(config-crypto-map)#set transform-set TSET Router(config-crypto-map)#exit
Step 6. Apply – Apply the cypto map to an interface.
Router(config)#int fa0/0 Router(config-if)#crypto map CMAP *Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Router(config-if)# Router(config-if)#do write Building configuration... [OK] Router(config-if)#
Now repeat the above steps on Router1:
Configuration on Router1
Router(config)#router rip Router(config-router)#network 10.0.0.0 Router(config-router)#network 192.168.2.0 Router(config-router)#
Router(config-isakmp)#authentication pre-share Router(config-isakmp)#hash sha Router(config-isakmp)#encryption aes 256 Router(config-isakmp)#group 2 Router(config-isakmp)#lifetime 86400 Router(config-isakmp)#exit
Router(config)#crypto isakmp key redhat address 10.0.0.1 Router(config)#crypto ipsec transform-set TSET esp-aes esp-sha-hmac Router(config)#access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255 Router(config)#crypto map CMAP 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured.
Router(config-crypto-map)#set peer 10.0.0.1 Router(config-crypto-map)#match address 101 Router(config-crypto-map)#set transform-set TSET Router(config-crypto-map)#exit
Router(config)#int fa0/0 Router(config-if)#crypto map CMAP *Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Router(config-if)#do write Building configuration... [OK] Router(config-if)#
Verification on Router0
Test and Verify IPSEC Configuration
Router#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id slot status 10.0.0.2 10.0.0.1 QM_IDLE 1089 0 ACTIVE
Router# show crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: CMAP, local addr 10.0.0.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer 10.0.0.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1, #pkts encrypt: 1, #pkts digest: 0
#pkts decaps: 2, #pkts decrypt: 2, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.0.0.1, remote crypto endpt.:10.0.0.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x34284297(875053719)
inbound esp sas:
spi: 0x196C4D5C(426528092)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: FPGA:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4525504/3535)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x34284297(875053719)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: FPGA:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4525504/3535)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
You can also Read:
How to Configure VPN on Cisco Router.
Discover more from Learn Linux CCNA CCNP CEH CISSP CISA Penetration-Testing Bug Bounty IPv6 Cyber-Security Network-Security Online
Subscribe to get the latest posts to your email.
Sir may i continue
On 24 Mar 2017 11:33, “Learn Linux CCNA CEH CCNP IPv6 Windows” wrote:
> satish tiwary posted: “Learn how to configure IPSEC site to site vpn on > cisco router using cisco Packet Tracer.As we all know IPsec provides secure > transmission of sensetive data over unprotected networks like internet.So > what actually IPsec does is it acts at the network layer” >
LikeLike
May i continue the classes ser
LikeLike
ofcourse you can!
LikeLike
not working! no isakmp and no outbound ESP from both routers.
LikeLike